Revolutionizing application security with the next-gen HAProxy Enterprise WAF
Explore the groundbreaking Intelligent WAF Engine and the key performance metrics that redefine industry standards.
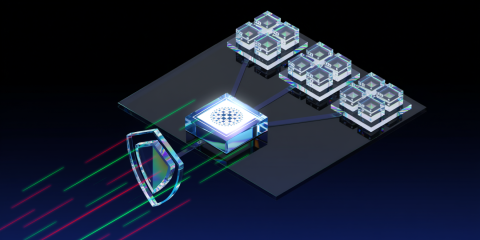
Explore the groundbreaking Intelligent WAF Engine and the key performance metrics that redefine industry standards.

Learn how to load balance VMware Horizon's complex UDP and TCP traffic using HAProxy's stateless stickiness. Improve remote desktop performance and reliability.

Different load balancer form factors don't always perform nor repackage well. Learn how HAProxy's unique software-first approach addresses common pain points when choosing the right form factor.

In this guide, we’ll explain why connection data matters. Next, we'll cover how the PROXY protocol works, how to use the TShark analyzer to capture and inspect packets and view the extraction results.

In this blog, you will learn what algorithm is the best for you, both static and dynamic algorithms will help you manage incoming traffic for web applications.

In this blog post, we will explore the gold standard of high availability and the difference between a forward proxy and a reverse proxy.

In this blog post, you’ll learn about several metrics that stand out as particularly useful for monitoring the health of your applications when they’re load balanced by HAProxy.

Let’s consider one of HAProxy’s newest features, dynamic servers, which lets you add and remove servers from HAProxy’s load balancing list on-the-fly without ever reloading the process.

Load balancing is the distribution of network traffic between backend servers to ensure high availability and performance. Here's everything you should know.

If you use HAProxy 2.0 or up, you must update to the latest version. A vulnerability was found that makes it possible for an attacker to...

In this blog post, you will learn how to enable service discovery for AWS EC2 instances using HAProxy and the HAProxy Data Plane API.

In this blog post, you'll learn how to run our Kubernetes Ingress Controller externally to your Kubernetes cluster, which obviates the need for running another load balancer in front.

In this blog, you will learn how to integrate HAProxy and Consul by using the HAProxy Data Plane API, which enables dynamic load balancer configuration changes.

In this blog post, we’ll walk through all of the steps necessary to get your HAProxy metrics displayed in InfluxDB.

In this blog post, we will describe how to implement autoscaling of your application pods using KEDA and the HAProxy Kubernetes Ingress Controller.

Choosing HAProxy as the proxy technology in your Consul service mesh means you’re running a high-performance solution and reducing latency between services.

First ever software load balancer exceeds 2 million RPS on a single Arm instance! We're near an era where you get the world’s fastest load balancer for free.

In this blog post, we’ll see how placing your servers behind HAProxy and using it as an API gateway lets you narrow the point of entry for attackers.
![Using HAProxy as an API Gateway, Part 6 [Security]](https://cdn.haproxy.com/img/containers/partner_integrations/api-gateway-security.png/809caaf409b9cbba5f53d22b31c00307/api-gateway-security.png)
In this post, you will learn how to leverage tokens to grant some users more access than others and then charge for the service. It's called API monetization.
![Using HAProxy as an API Gateway, Part 5 [Monetization]](https://cdn.haproxy.com/img/containers/partner_integrations/api-gateway-monetization.png/f6ba7bc74399bb3dbeaec96f2813c2f7/api-gateway-monetization.png)
The HAProxy Kubernetes Ingress Controller has two sources of logs: the controller and the HAProxy load balancer. Both can be customized.
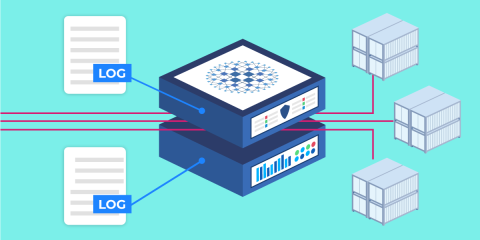
In this blog post, you'll learn about the metrics which HAProxy compiles, how to extract them with Prometheus, and visualize them with Grafana or Kibana.
![Using HAProxy as an API gateway, part 4 [metrics]](https://cdn.haproxy.com/img/containers/partner_integrations/api-gateway-4-metrics.png/bead5c0427ca39dcc7c44ed61225e630/api-gateway-4-metrics.png)
In this blog post, you'll learn how to implement a circuit breaker with HAProxy in a simple and more complex way, that allows greater customization.
In this blog post, you will learn several ways to configure HAProxy for proxying SSH, all of which rely on the ssh command's ProxyCommand field.

In this blog post, you will learn more about persistent TCP connections in an HTTP world and the various ways in which HAProxy supports it.

Log Sampling is a powerful feature introduced in HAProxy 2.0 that lets you create a representative view of your data allowing you to minimize your costs.

Learn how to set up HAProxy's cache feature, which will improve how fast you can deliver messages and lessen the load placed upon your backend servers.

HTTP Strict Transport Security (HSTS) sends a user to the secure version of a site without an HTTP redirect. Learn how to enable HSTS with HAProxy.

Read on to learn how to use the HAProxy load balancer to redirect users from HTTP to HTTPS automatically in a few easy steps.

Find out how you can detect and stop fake web crawlers by using Verify Crawler add-on which comes included with the HAProxy Enterprise license.

In the blog post, you will learn how to become FIPS compliant using Red Hat Enterprise Linux 8 and HAProxy Enterprise for TLS encryption.

Learn how to use the dynamic SSL certificate storage introduced in HAProxy 2.1 and expanded in HAProxy 2.2 in order to update SSL certificates dynamically.

In this blog post, you will learn how to use HAProxy's Deny, Tarpit, Silent Drop, Reject, and Shadowban response policies to stop threats and malicious users.

Learn how to configure TLS with the HAProxy Kubernetes Ingress Controller to provide secure communication to everyone accessing your Kubernetes services.
In this blog post, you will find out more about the HAProxy Process Manager, which allows you to start external programs that are hosted under HAProxy.

In this blog post, you’ll see how to combine HAProxy and Docker Swarm to load balance traffic across your service replicas.

Learn more about the HAProxy ALOHA PacketShield product, which provides stateful packet filtering and protects your network against DDoS.

Use rate limiting in HAProxy to stop clients from making too many requests and promote fair usage of your services.

Learn how to use the HAProxy Traffic Shadowing agent to enable traffic mirroring and stream production requests to a test environment.

HAProxy 2.0 introduced layer 7 retries, which provides resilience against unreachable nodes, network latency, slow servers, and HTTP errors.

Learn how the new HAProxy Kubernetes Ingress Controller provides a high-performance ingress for your Kubernetes-hosted applications.

This blog post shows you how to use the HAProxy Data Plane API to manage your load balancer configuration dynamically using HTTP commands.

Learn how to use DNS service discovery in HAProxy to detect server changes and automatically apply them to your configuration.

HAProxy integrates with AWS X-Ray to give you the best observability across your Amazon Web Services (AWS) resources, including your load balancer.
Learn to monitor, troubleshoot, and manage your load balancer effectively with our deep dive into the HAProxy status page.

In this blog, we’ll explain how to set up the metrics endpoint, how to configure Prometheus to scrape it and offer guidance on graphing and alerting the data.
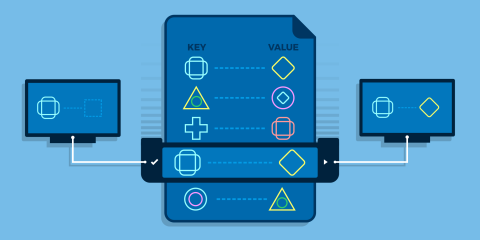
Learn how to use The HAProxy Stream Processing Offload Engine (SPOE) filter to extend HAProxy in any language without modifying its core codebase.

This blog post shows how to use HAProxy IP Masking in order to protect the privacy of your users, helping you to stay compliant with laws like the GDPR.

In the blog post, you'll learn various ways to health check your servers so that your APIs maintain a high level of reliability. This includes...
![Using HAProxy as an API gateway, part 3 [health checks]](https://cdn.haproxy.com/img/containers/partner_integrations/image2-2-%281%29.png/5ef4ef148b968f89804293c3d44312e7/image2-2-%281%29.png)
The Power of Two Random Choices load-balancing algorithm made us curious. See how it stacks up against other modern-day algorithms available in HAProxy.

In the blog post, you'll learn more about using HAProxy as an API gateway, leveraging it to secure your API endpoints using OAuth 2.
![Using HAProxy as an API Gateway, Part 2 [Authentication]](https://cdn.haproxy.com/img/containers/partner_integrations/image2-e1548174430466.png/3942e9fa498bb46e325ba72db6f9bd84/image2-e1548174430466.png)
Learn how to set up an example project that uses gRPC and Protocol Buffers to stream messages between a client and a server with HAProxy in between.

In a service mesh, requests are passed to proxies that relay messages from one service to another. See how HAProxy can be used in the Consul service mesh.

HAProxy has best-in-class bot protection capabilities for detecting and defending against many types of unwanted bot traffic. Read on to learn how.

In this post, you’ll learn how to create an HAProxy map file, store it on your system, reference it in your HAProxy configuration, and update it in real time.
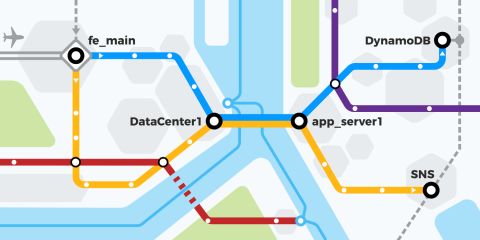
In this blog post, we'll demonstrate how to place HAProxy at the edge of your AWS infrastructure without involving Elastic Load Balancing (ELB).

An API gateway routes client requests intelligently and handles functions such as load balancing, security, and rate limiting.
![Using HAProxy as an API gateway, part 1 [introduction]](https://cdn.haproxy.com/img/containers/partner_integrations/2022/api-gateway-pt1/avalanche-area-1080x540.png/2b915c11c726470bf6e314e194c3a7ed/avalanche-area-1080x540.png)
A practical guide to HAProxy ACLs. Learn the syntax and follow step-by-step examples to block traffic, redirect users, choose backends, and enhance security.

In this blog post, we will show you a zero-touch method for integrating HAProxy with Consul by using DNS for service discovery available in HAProxy 1.8.

In this blog post, we'll demonstrate how to use HAProxy in combination with Amazon Elastic Load Balancing (ELB) and Amazon Application Load Balancer (ALB).

Microservices architectures require the ability to make frequent app delivery changes in an automated and reliable way. The HAProxy Runtime API enables this.

Why use the Proxy protocol? Well, when you lose client information like IP address when relaying connections through proxies, this tends to prevent you from...

This is the ALOHA Pocket. Probably the smallest load balancer you have ever seen from any vendor.

In a Slow POST attack, an attacker begins by sending a legitimate HTTP POST header to a Web server, exactly as they would under normal circumstances.

In this blog post, we will give a quick step-by-step guide on how to serve ECC and RSA certificates on the same IP with HAProxy.

Remote Desktop Services is a technology from Microsoft that allows users to remotely access a session-based desktop, virtual machine-based desktop, or...

Health checking is one of the most important features of a load balancer. Here we show how to match multiple conditions for HTTP health checking in HAProxy.

This blog post explains how to use HAProxy to simply prevent using SSLv3 or to prevent those users to reach your applications and print them a message.

Today’s article will explain how to use HAProxy to protect your application from Bash shellshock vulnerability if you’re in a case where you have to be protected.

In this blog post, we demonstrate how to enable binary health checks with HAProxy 1.5 by using a PHP-fpm/FastCGI probe example.

Some customers ask us to migrate the Apache mod_proxy configuration into HAProxy. This article explains how to translate ProxyPass-related rules.

In this blog post, we will demonstrate how to perform asymmetric routing and multiple default gateways on Linux with HAProxy.

You don’t want your clients to send their cookies (understand their identity) clearly through the Internet. This is today’s article's purpose.

In this blog post, we will show the different ways in which you can use the HAProxy load balancer to emulate an active/passive clustering mode.

In this blog post, we demonstrate how to build a simple Redis infrastructure thanks to the HAProxy advanced send/expect health checks feature.

HAProxy allows to redirect traffic based on events and internal status. In this blog post we show how to use HAProxy for failover and worst-case management.

Here comes the transparent proxy mode: HAProxy can be configured to spoof the client IP address when establishing the TCP connection to the server.

A brute force attack in WordPress consists of massively sending requests to a URL with different parameters each time. Here's how to prevent it using HAProxy...

In this blog post, we show two ways of performing source IP affinity with HAProxy: through the hash load balancing algorithm and using HAProxy Stick Tables.

When setup by the application server, the HAProxy load balancer can be used to update cookies on-the-fly. In this blog post, we explain how.

The BEAST attack on SSL isn’t new, but we have not yet published an article to explain how to mitigate it with ALOHA or HAProxy.

In this blog post, we show how to perform load balancing with HAProxy on Microsoft Exchange 2013 Services hosted on single and multiple host names.

In this blog post, we show how to use HAProxy with MySQL at high request rates, and how to prevent the common TCP source port exhaustion error.

In this blog post, we will provide information on how to enable Exchange Outlook Web Access (OWA) Cross-Site Request Forgery (CSRF) protection with HAProxy.

HTTP protocol is connection-less and only the client can request information from a server. In any case, a server can contact a client. Furthermore...

In this blog post, we will demonstrate how to create a highly performant WAF platform using Naxsi and the HAProxy load balancer.

The below information is deprecated as HAProxy Enterprise now offers a fully functional native WAF module which supports whitelist-based rulesets, and more.

In this blog post, we will show how to use HAProxy's layer 7 features to improve eCommerce website performance and provide the best end-user experience.

HAProxy is a high-performance reverse proxy and load balancer commonly used on web platforms and even as a replacement for hardware load balancers like F5 appliances.

In this blog post, we'll explain how to use both HAProxy and Varnish on a web application hosted on a single domain name.

Slowloris is a script which opens TCP connections and sends HTTP headers very slowly to force web servers to keep connections opened. The purpose is to...
