The state of web app, API, and AI service security is in constant flux, with threats seemingly lurking around every corner. For years, organizations have relied on web application firewalls (WAFs) as a critical layer of defense. HAProxy Technologies has long provided robust WAF solutions, including earlier versions such as the "Advanced WAF" and "ModSecurity WAF" — based on the popular open source WAF engine. These excelled against widely-known OWASP Top 10 threats.
However, cyber threats with increasingly complex attack vectors and new zero-day exploits have grown more sophisticated — and elusive. Reactive, signature-based defenses now leave critical blind spots that bad actors can readily exploit. In response, our team has engineered a smart, new approach to application security – one capable of defending against sophisticated threats while simultaneously reducing false positives, simplifying management, and delivering performance efficiency that makes advanced security virtually cost-free.
We officially introduced the next-gen HAProxy Enterprise WAF with HAProxy Enterprise 2.9, and since then it has become a stable and mature option used by some of our biggest enterprise customers. This new WAF is designed to address the complexities and demands of modern application environments and the advanced threats they face — and is distinguished by its exceptional balanced accuracy, simple management, and ultra-low latency and resource usage.
Next, we'll dive (but not too deeply!) into the innovations behind the HAProxy Enterprise WAF. We'll explore the groundbreaking Intelligent WAF Engine, share key performance metrics that redefine industry standards, detail its unmatched usability, and outline its comprehensive protections. This thorough overview will show how this next-gen WAF empowers organizations to secure their services with unprecedented confidence and efficiency.
HAProxy Edge provides a globally distributed application delivery network for fully managed application delivery and security services and a secure partition between external traffic and origin networks. HAProxy Edge uses the same high-performance WAF as HAProxy Enterprise, along with a high-capacity global network that delivers full-spectrum DDoS protection, bot management, accelerated content delivery, and a comprehensive observability suite.
Beyond signatures: introducing the Intelligent WAF Engine
Traditional WAFs have historically relied on static lists and regex-based attack signatures to identify and block malicious traffic. Unfortunately, these measures are only capable of detecting threats for which a signature already exists. This leaves organizations vulnerable to emerging, polymorphic, or previously unseen attacks — commonly called zero-day threats. The unending race to update signatures against rapidly evolving threats also imposes a significant operational burden on security teams.
The patent-pending, next-gen HAProxy Enterprise WAF is built on our unique Intelligent WAF Engine. This engine moves beyond the constraints of static signatures by employing a non-signature-based detection system. Its advanced threat detection is powered by threat intelligence data from over 60 billion daily requests on HAProxy Edge and enhanced by machine learning — delivering highly accurate threat detection that virtually eliminates false alarms and undetected threats with almost zero performance impact on legitimate traffic. Our data science team trains our security models and enables them to reliably detect any attacks and anomalous behavior.
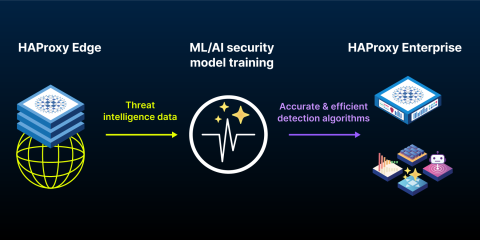
This proactive, adaptive protection enables HAProxy Enterprise WAF to identify and block emerging and elusive threats without requiring users to manually create, maintain, or update rules other than simple allow-lists. This architectural shift towards a more intelligent and anticipatory security posture offers better protection and improved operational efficiency.
Unmatched accuracy and performance
A WAF's effectiveness is ultimately measured by its ability to accurately distinguish between legitimate and malicious traffic, all without notably impacting app performance. Accordingly, the next-gen HAProxy Enterprise WAF sets new standards for exceptional accuracy and speed.
WAF accuracy can be calculated by measuring the true positive rate and the true negative rate:
True-positive rate refers to the proportion of dangerous traffic correctly identified by the WAF. Dangerous traffic incorrectly identified as safe is a “false negative”.
True-negative rate refers to the proportion of safe traffic correctly identified by the WAF. Safe traffic incorrectly identified as dangerous is a “false positive”.
The average of these two values is called “balanced accuracy”. The vast majority of WAFs on the market do well at one metric but not the other, resulting in poor scores for balanced accuracy (generally below 90%).
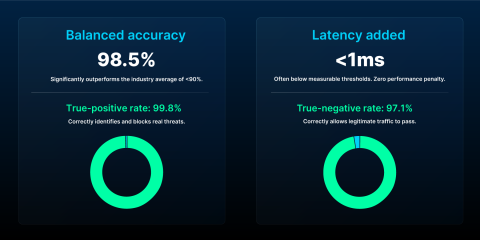
Open source benchmarks reveal the HAProxy Enterprise WAF's impressive accuracy rates: a 99.8% true-positive rate (indicating its efficacy in accurately identifying actual threats) and a 97.1% true-negative rate (signifying its ability to allow legitimate traffic through). These equate to an outstanding balanced accuracy rate of 98.5%. This significantly outperforms the category average, which typically falls below 90%. HAProxy Enterprise WAF thus ensures full-spectrum threat coverage, drastically minimizes false alarms, and ensures a seamless user experience.
Next comes performance. HAProxy Enterprise adds under 1ms of latency to each request on average, and that doesn’t change when you enable the HAProxy Enterprise WAF – it’s one of the only WAFs that runs in the same process as the request, having virtually no impact on performance. In the vast majority of cases, any added latency is below measurable thresholds — meaning no more tradeoffs between security and speed. This ensures a highly responsive user experience and optimal service performance under all traffic loads, making your business and customers happy.
What’s more, this performance is achieved with startling efficiency. HAProxy has always been known for its low resource usage, and with HAProxy Enterprise WAF, that doesn’t change. In fact, enabling HAProxy Enterprise WAF has virtually no impact on CPU usage, according to customers like Roblox who presented their use case and experience at HAProxyConf.
At HAProxyConf 2025, Ben Meidell, Sr. Site Reliability Engineer at Roblox, showed how the immersive gaming and creation platform uses hundreds of HAProxy instances to manage and secure millions of requests per second. Commenting on the efficiency of HAProxy Enterprise WAF, Meidell said, “One of the big points about scaling up a web application firewall is the potential impact. We have been extremely impressed with the performance of HAProxy Enterprise WAF. When we first activated it, CPU increase was so negligible that I wondered if I’d made a mistake somewhere. But then I saw all the violations it was catching and realized just how effective it was.”
Another notable feature is the optional OWASP Core Rule Set (CRS) compatibility mode. This caters to organizations that require OWASP CRS support for specific use cases or compliance. When enabled, this mode introduces fifteen times lower added latency, on average, versus our previous ModSecurity WAF using the OWASP CRS — even under mixed traffic conditions. This direct, quantifiable comparison against the most widely adopted open source WAF implementation highlights how far our security engineers were able to push performance.
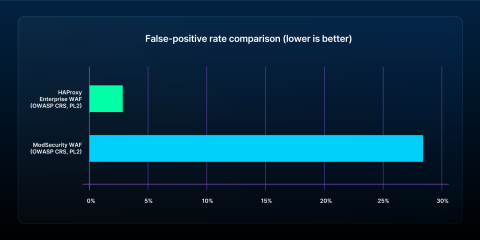
Plus, HAProxy Enterprise WAF generates significantly fewer false positives with OWASP CRS enabled: an impressively low 2.9% false-positive rate at paranoia level 2, greatly outperforming the 28.36% figure for the ModSecurity WAF under identical conditions. This dramatic improvement has been a great relief to teams otherwise saddled with operational overhead and alert fatigue from traditional ModSecurity implementations.
Also at HAProxyConf 2025, Juraj Ban, Principal Security Architect at Infobip, explained how HAProxy Enterprise WAF solved the twin problems of latency and false positives: “The engine is powerful and fast. We don't have any latency issues anymore. We don't have any false positives, and when we set up a new application we don’t need to fine-tune the WAF rules. We don't have complaints from our customers — that is the most important thing!”
Simpler security with enhanced control
Teams have historically viewed WAFs as complex, resource-intensive, and high maintenance — requiring extensive tuning. As a result, they haven't rushed to adopt and manage these solutions. HAProxy Enterprise WAF addresses these pain points by offering simplicity and control.
Because users don’t need to manually write, configure, or continuously maintain complex custom rules, adoption and management aren't insurmountable tasks. It makes intelligent WAF protection more accessible and practical for a broader range of organizations — from those with smaller security teams or less specialized WAF expertise, to large enterprises that need to reduce the operational overhead of managing hundreds or thousands of WAFs.
For those organizations with more complex needs, HAProxy Enterprise WAF makes it simple to deploy differentiated WAF rules using customizable WAF Profiles (available in HAProxy Enterprise 3.2). You can now create, customize, and apply a unique WAF ruleset for each WAF Profile, applying them selectively across different applications or locations. This granular control is essential for tailoring security across diverse application portfolios. By fine-tuning WAF security based on the unique traffic patterns and security requirements of individual applications, you can minimize false positives, reduce alert fatigue, and ensure an improved UX for your legitimate users.
WAF management and observability are streamlined through HAProxy Fusion, the centralized control plane for HAProxy Enterprise. HAProxy Fusion simplifies WAF management across diverse and complex environments, including multi-cluster, multi-cloud, and multi-team deployments. Teams get a unified WAF management interface which lets them upload custom rulesets, set thresholds, add exceptions when needed, and view security responses individually — or globally — across their load balancing clusters.
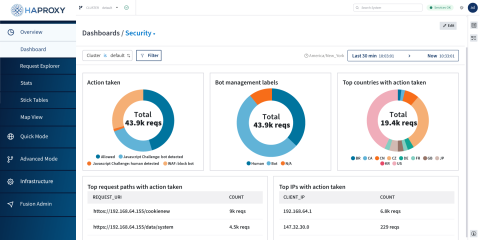
Comprehensive protection for modern services
HAProxy Enterprise WAF effectively guards against a broad range of threats, including $SQL (SQL injection), $XSS (cross-site scripting), $RCE (remote code execution), $RFI (remote file inclusion), $TRAVERSAL (directory traversal attacks), and $EVADE (defense evasion attempts). The Intelligent WAF Engine adds robust protection against emerging and elusive zero-day threats, helping thwart attacks that traditional signature-based systems would miss.
Zooming out, HAProxy Enterprise WAF is not merely an isolated security product but an integral component of HAProxy Enterprise’s multi-layered security suite. This suite includes other critical security features such as HAProxy Enterprise Bot Management Module and global rate limiting — powered by the Global Profiling Engine (GPE). Modern cyberattacks are often multi-staged and involve many attack vectors, from automated bot reconnaissance to Layer 7 exploits. Singular security features cannot possibly address every cyber threat.
For example, HAProxy Enterprise Bot Management Module can identify and reroute bad traffic before it even reaches HAProxy Enterprise WAF, boosting performance against application-layer attacks and minimizing load. This integrated approach is highly customizable, robust, and enables defense-in-depth threat management strategies. It's also a strong value proposition for customers seeking a unified security platform.
Benefits for your organization
The advanced technical capabilities of the next-gen HAProxy Enterprise WAF translate into improved efficiency, cost savings, and enhanced user experiences. Threat detection and traffic filtering occur in microseconds, resulting in minimal resource consumption and substantially lower operational costs. Plus, the near-absence of false positives — as demonstrated by the impressive 2.9% false-positive rate when using the OWASP CRS — drastically reduces the operational burden for security teams. Spend less time triaging irrelevant alerts and more time focusing on strategic security initiatives that can directly reduce risk and expenses.
Don't forget about accuracy. By virtually eliminating false negatives — where malicious traffic is missed — HAProxy Enterprise WAF helps minimize downtime, data loss, financial fraud, and other negative outcomes. Its comprehensive protection against today's and tomorrow's threats keeps you protected. You've worked hard to maintain a solid business reputation, and your WAF should support you there.
Neither humans nor legitimate bots (such as Googlebot) are inadvertently blocked nor encounter latency. The HAProxy Enterprise WAF operates as a highly accurate detection and signaling system, allowing you to define your own response — whether that means blocking, logging, or alerting. This flexibility ensures seamless application delivery, positively impacts business perception, and increases ROI through risk mitigation and operational efficiency.
Why upgrade now?
The case for adopting the next-gen HAProxy Enterprise WAF is clear. When threats are sophisticated and application performance is critical, relying on outdated or inefficient security solutions poses clear (and unnecessary) risks.
HAProxy Enterprise WAF offers unmatched accuracy, uncompromising performance with ultra-low latency and resource usage, simple management, and next-gen threat protection. For organizations currently grappling with the operational overhead of traditional WAFs, the alert fatigue from high false positives, or the constant threat of zero-day exploits, HAProxy Enterprise WAF will be transformative.
Try HAProxy Enterprise WAF today
To further explore how our WAF solution can secure web apps, APIs, and AI services, check out our web application firewall solution page. For deeper insights into specific use cases or to see HAProxy Enterprise WAF in action, we encourage you to contact our team.
Subscribe to our blog. Get the latest release updates, tutorials, and deep-dives from HAProxy experts.




