Announcing HAProxy 3.3
HAProxy 3.3 brings downloadable packages compiled by HAProxy Technologies, numerous TLS enhancements, better observability, and many improvements to performance and flexibility.


Baptiste Assmann is Director of Product at HAProxy Technologies. An expert in load balancing and high-performance architectures, he plays a key role in HAProxy's evolution within the Cloud Native ecosystem. A regular speaker, he shares his expertise on the scalability and security of modern applications.
Twitter LinkedIn GitHubHAProxy 3.3 brings downloadable packages compiled by HAProxy Technologies, numerous TLS enhancements, better observability, and many improvements to performance and flexibility.

This year at Black Hat USA, the conversation focused on model context protocol (MCP), agentic workflows, and how security fundamentals still matter.

HAProxy 3.2 gives you more of what matters most: exceptional performance and efficiency, best-in-class SSL/TLS, deep observability, and flexible control over your traffic.

HAProxy ALOHA 17.0 introduces the new UDP Module and extends network management to the Data Plane API, a new API-based approach to network configuration.

HAProxy Enterprise 3.1 delivers a brand new ADFSPIP Module and enhancements to the HAProxy Enterprise UDP Module, CAPTCHA Module, Global Profiling Engine, and more!

HAProxy 3.1 brings improvements to observability, reliability, performance, and flexibility.

HAProxy Enterprise 3.0 extends HAProxy Enterprise’s legendary performance and flexibility and builds upon its cornerstone features.

Our implementation of the HTTP/2 protocol can effectively handle the CONTINUATION Flood.

In this blog post, you will learn more about persistent TCP connections in an HTTP world and the various ways in which HAProxy supports it.

Learn how to use DNS service discovery in HAProxy to detect server changes and automatically apply them to your configuration.

In the blog post, you'll learn various ways to health check your servers so that your APIs maintain a high level of reliability. This includes...
![Using HAProxy as an API gateway, part 3 [health checks]](https://cdn.haproxy.com/img/containers/partner_integrations/image2-2-%281%29.png/5ef4ef148b968f89804293c3d44312e7/image2-2-%281%29.png)
In the blog post, you'll learn more about using HAProxy as an API gateway, leveraging it to secure your API endpoints using OAuth 2.
![Using HAProxy as an API Gateway, Part 2 [Authentication]](https://cdn.haproxy.com/img/containers/partner_integrations/image2-e1548174430466.png/3942e9fa498bb46e325ba72db6f9bd84/image2-e1548174430466.png)
In a service mesh, requests are passed to proxies that relay messages from one service to another. See how HAProxy can be used in the Consul service mesh.

An API gateway routes client requests intelligently and handles functions such as load balancing, security, and rate limiting.
![Using HAProxy as an API gateway, part 1 [introduction]](https://cdn.haproxy.com/img/containers/partner_integrations/2022/api-gateway-pt1/avalanche-area-1080x540.png/2b915c11c726470bf6e314e194c3a7ed/avalanche-area-1080x540.png)
In this blog post, we will show you a zero-touch method for integrating HAProxy with Consul by using DNS for service discovery available in HAProxy 1.8.

The monumental stable release of HAProxy 1.8 is here! The HAProxy 1.8 release candidate 1 (RC1) has been published by the R&D team here at HAProxy Technologies.

This blog contains information and provides a technical guide for getting started with the ELK stack, configuring HAProxy, parsing the data and troubleshooting.

In a Slow POST attack, an attacker begins by sending a legitimate HTTP POST header to a Web server, exactly as they would under normal circumstances.

In this blog post, we will answer this question: how to follow up on a container IP change when restarting a container?

13th of October 2015, Willy Terrau announced the release of HAProxy 1.6.0, after 16 months of development. A total of 1156 commits from 59 people were committed.

In this blog post, we will show how to use HAProxy's hash based load balancing algorithm for static content delivery with Varnish.

Remote Desktop Services is a technology from Microsoft that allows users to remotely access a session-based desktop, virtual machine-based desktop, or...

Health checking is one of the most important features of a load balancer. Here we show how to match multiple conditions for HTTP health checking in HAProxy.

This blog post explains how to use HAProxy to simply prevent using SSLv3 or to prevent those users to reach your applications and print them a message.

Today’s article will explain how to use HAProxy to protect your application from Bash shellshock vulnerability if you’re in a case where you have to be protected.

In this blog post, we demonstrate how to enable binary health checks with HAProxy 1.5 by using a PHP-fpm/FastCGI probe example.

The HTTP 408 status code is an error returned by the server when it doesn't receive a timely request from the client.

Some customers ask us to migrate the Apache mod_proxy configuration into HAProxy. This article explains how to translate ProxyPass-related rules.

In this blog post, we will demonstrate how to perform asymmetric routing and multiple default gateways on Linux with HAProxy.

You don’t want your clients to send their cookies (understand their identity) clearly through the Internet. This is today’s article's purpose.

In this blog post, we will show the different ways in which you can use the HAProxy load balancer to emulate an active/passive clustering mode.

In this blog post, we demonstrate how to build a simple Redis infrastructure thanks to the HAProxy advanced send/expect health checks feature.

HAProxy allows to redirect traffic based on events and internal status. In this blog post we show how to use HAProxy for failover and worst-case management.

Basically, HAProxy uses the NPN (and later the ALPN) TLS extension to figure out whether the client can browse the website using SPDY.

Here comes the transparent proxy mode: HAProxy can be configured to spoof the client IP address when establishing the TCP connection to the server.

In this blog post, we show how you can enable inserting client certificate information in HTTP headers and reporting them in the log line with HAProxy.

In this blog post, we provide an HAProxy configuration that can help you detect the Apache Cdorked Backdoor attack in your systems and protect them against it.

A brute force attack in WordPress consists of massively sending requests to a URL with different parameters each time. Here's how to prevent it using HAProxy...

In this blog post, we show two ways of performing source IP affinity with HAProxy: through the hash load balancing algorithm and using HAProxy Stick Tables.

In this blog post, we describe how you configure HAProxy to log URLs exactly the way they were sent by the client by using syslog-ng's flexible configuration.

When setup by the application server, the HAProxy load balancer can be used to update cookies on-the-fly. In this blog post, we explain how.

Performing SSL at the Load-Balancer Layer is called SSL offloading because you offload this process from your application servers. Here's what you should know.

The BEAST attack on SSL isn’t new, but we have not yet published an article to explain how to mitigate it with ALOHA or HAProxy.

In this blog post, we show how to perform load balancing with HAProxy on Microsoft Exchange 2013 Services hosted on single and multiple host names.

In this blog post, we show how to use HAProxy with MySQL at high request rates, and how to prevent the common TCP source port exhaustion error.

In this blog post, we will provide information on how to enable Exchange Outlook Web Access (OWA) Cross-Site Request Forgery (CSRF) protection with HAProxy.

HTTP protocol is connection-less and only the client can request information from a server. In any case, a server can contact a client. Furthermore...

This guide shows you how to use the 'log-format' directive, variables, and captured headers to create the perfect log for your needs.

Compression is used for reducing object size in order to reduce delivery delay for objects over the HTTP protocol. We show how to enable this in HAProxy.

In this blog post, we will demonstrate how to create a highly performant WAF platform using Naxsi and the HAProxy load balancer.

The below information is deprecated as HAProxy Enterprise now offers a fully functional native WAF module which supports whitelist-based rulesets, and more.

The main purpose of using client-side certificates is to increase the level of authentication. Since HAProxy is often in front of web platform, it is the right place to do this authentication.

In this blog, we share how to build a high-available RTMP platform for delivering video content with HAProxy and crtmpserver.

In this blog post, we will show how to use HAProxy's layer 7 features to improve eCommerce website performance and provide the best end-user experience.

HAProxy is a high-performance reverse proxy and load balancer commonly used on web platforms and even as a replacement for hardware load balancers like F5 appliances.

HAProxy can support SSL offloading. Today, I’ll focus on how to install and configure HAProxy to offload SSL processing from your servers.

In this blog post, we'll explain how to use both HAProxy and Varnish on a web application hosted on a single domain name.

Despite being “competitors”, each of them has its own very well performing: HAProxy is a Reverse-proxy Load-Balancer and Varnish is a Reverse-proxy cache.

In this blog post, we will provide a configuration that you can use to protect your applications against HTTP request flood attacks.

Geolocation is the process of linking a third party to a geographical location. In easier words: know the country of a client's IP address. On the Internet, such a base is called GeoIP.

In this blog post, we will explain how to configure the HAProxy load balancer to build an efficient SMTP relay infrastructure with Postfix.

In this blog post, we aim to demonstrate how to preserve source IP addresses when using the reverse-proxy mode in HAProxy.

In this blog post, we summarize the findings of a hypervisors virtual network performance comparison from a virtualized load balancer point of view.

In this blog post, we show how to enable enhanced SSL load balancing with the Server Name Indication (SNI) TLS Extension in HAProxy and HAProxy ALOHA.

This blog post shows why and how to use a load balancer, the differences between Affinity, Persistence, and Sticky Sessions, and how to enable them in HAProxy.

Microsoft Terminal Services or remoteapps both use the RDP protocol. One issue when using RDP is being able to stick a user to a server.

This blog post will show you how to use HAProxy ALOHA as a reverse proxy for accessing multiple websites or apps behind a single public IP address.

In this blog post, we explain how one can improve SSL/TLS performance by adding some functionality to SSL open-source software with HAProxy.

In this blog post, we explain what the Layer 4 Load Balancing Direct Server Return (DSR) Mode is, its pros and cons and when and how to use it.

In this blog post, we explain what the Layer 4 load balancing tunnel mode is, how it works, when to use it, as well as its pros and cons.

In this blog post, we explain what the Layer 4 Load Balancing NAT Mode is, its pros and cons and when to use this type of architecture.

In this blog post we will demonstrate how you can send users to the same server for imap and smtp by using HAProxy ALOHA.

Your application uses both HTTP and HTTPS, depending on the pages. SSL encryption is achieved by your backend server directly. Here's how.

Slowloris is a script which opens TCP connections and sends HTTP headers very slowly to force web servers to keep connections opened. The purpose is to...

HAProxy ALOHA allows you to maintain HTTPS sessions based on SSL connection ID. In this blog post, we show you how to configure HAProxy ALOHA for this.

In this blog post we demonstrate how to protect any application or web server against unexpected high load using HAProxy ALOHA.

Build a scalable architecture for a news website using these components: A load balancer with content switching capability, cache server and application server.

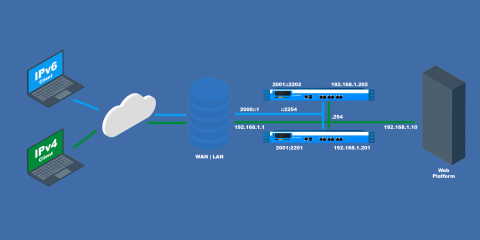
In this blog post, we show how to configure HAProxy Aloha to use it as an IPv6 to IPv4 gateway without modifying anything on your current platform.
Layer 4 is related to the transport layer of the OSI model, and layer 7 is related to the application level. A layer 7 load balancer makes routing decisions based on...
