Also called "re-encryption," SSL/TLS bridging involves decrypting incoming HTTPS traffic and then re-encrypting it before forwarding to the server. Bridging lets users establish a secure connection with the load balancer via a frontend certificate. The load balancer's backend then forms a newly secured connection before re-encrypting those requests via the backend certificate.
How does SSL/TLS bridging work?
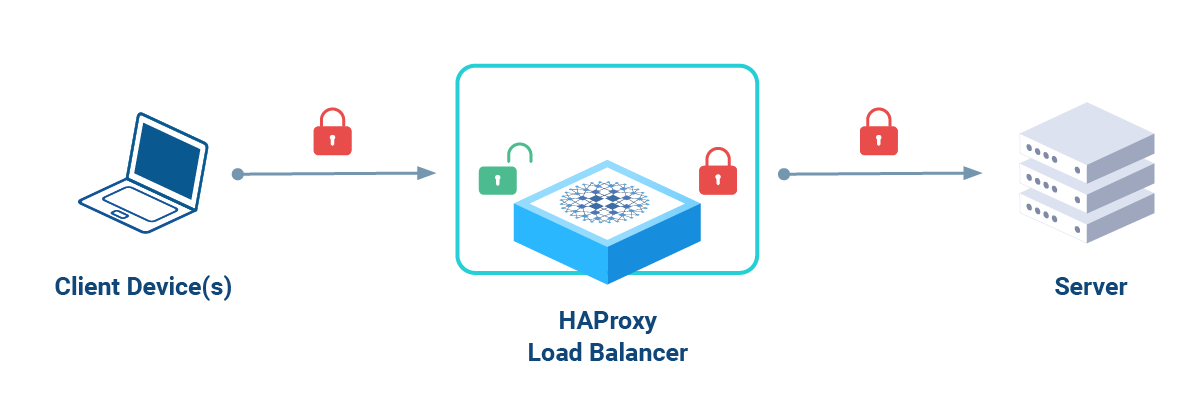
First, the load balancer receives requests over an SSL connection that was previously established using a symmetric cipher and shared keys. The client and load balancer exchange these components once the secure connection is created. It's also only known to those two parties, which maintains secrecy.
Next, the certificate employs one of many cryptographic methods to protect forwarded requests from man-in-the-middle (MITM) attacks as they approach backend servers. This is often based on a vital combination of user IDs and public keys, which are codependent and form a trusting relationship between authorized parties.
Does HAProxy support SSL/TLS bridging?
Yes! Though we don't refer to it as such internally. HAProxy supports SSL/TLS between the load balancer and servers using a certificate and private key. To learn more about our implementation, read our TLS documentation.
