Layer 4 (LVS)
Direct Server Return
Use Direct Server Return to have responses from backend servers bypass HAProxy ALOHA and go directly to the client, improving performance.
Direct Server Return, also known as Direct Routing, is a good option when you need to service a high volume of traffic, since it prevents the HAProxy ALOHA from becoming a bottleneck for packets that are returning to the client. While packets flow through the HAProxy ALOHA on their way from the client to the backend servers, they skip the HAProxy ALOHA on their way back to the client. You accomplish this by configuring each backend server’s default gateway to be the network’s external gateway.
In this configuration, which does not use NAT, the destination IP address is not changed. So, the backend server must receive traffic on the same IP address as the one on which the HAProxy ALOHA listens, and that the client originally requested. Doing so is easiest on Linux backend servers because they provide a special loopback interface that can be configured with an IP alias (virtual IP). Windows servers do not define a loopback interface.
The advantages of this mode include the ability to service a high volume of traffic efficiently, such as video and audio streams. The disadvantages of this mode include needing to configure the backend server’s loopback interface in a special way to listen on a virtual IP address (IP alias), the need to manage ARP replies so that the network does not detect an IP conflict, and that the HAProxy ALOHA is unable to log responses from servers. This mode is not well supported on Windows servers due to Windows not defining a loopback interface.
This mode can be used only when load balancing traffic via the LB Layer4 tab, which supports the raw TCP and UDP protocols.
Traffic flow Jump to heading
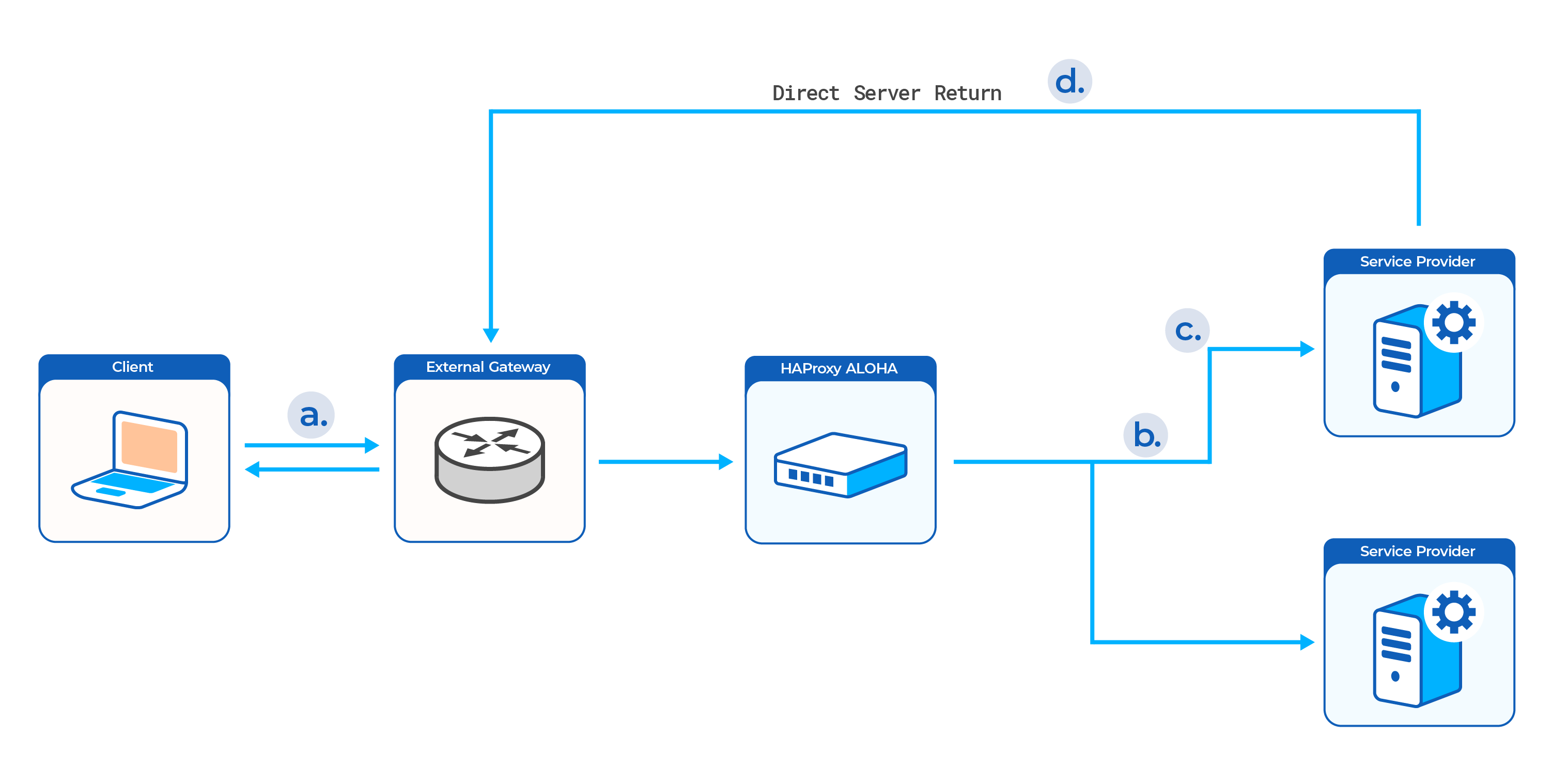
-
The client connects to your application at the configured public IP address. The HAProxy ALOHA listens at that address and receives the packets.
-
The HAProxy ALOHA routes unmodified packets to one of your backend servers.
Although any of the servers in the server farm may be chosen, and each listens on a unique private IP address, the packets themselves are not modified. Therefore, they still contain the ALOHA’s public IP address as the destination. The backend servers must be configured to receive traffic on this IP too. They accomplish this by setting up a virtual IP (IP alias) on a virtual interface (the loopback interface).
-
The backend server accepts the request on its private IP address and then forwards the packets to its loopback interface where the virtual IP matching the packet’s destination IP is configured. The loopback interface is a virtual interface found on Linux servers.
-
The server responds directly to the source IP address it finds in the packet, which is that of the client. Because the client’s IP address is outside of the local network, the response is sent to the network’s external gateway and then out, skipping the HAProxy ALOHA on the return.
Enable Direct Server Return Jump to heading
-
In the web UI’s LB Layer4 tab, add the
mode gatewaydirective to your existing configuration, and apply your changes.haproxydirector exchange 10.0.0.9:443 TCPbalance roundrobin # load balancing algorithmmode gateway # forwarding modecheck interval 10 timeout 2 # check parametersoption tcpcheck # adv check parametersserver exchange1 10.0.0.13:443 weight 10 check # server exchange1server exchange2 10.0.0.14:443 weight 10 check # server exchange2haproxydirector exchange 10.0.0.9:443 TCPbalance roundrobin # load balancing algorithmmode gateway # forwarding modecheck interval 10 timeout 2 # check parametersoption tcpcheck # adv check parametersserver exchange1 10.0.0.13:443 weight 10 check # server exchange1server exchange2 10.0.0.14:443 weight 10 check # server exchange2 -
On each backend server, assign the virtual IP to a loopback interface.
-
In the Setup tab, click Save under Local Configuration to persist your changes after a reboot.
Configure VIPs on Linux Jump to heading
The VIP must be handled on each server’s loopback interface to accept connections, but can’t be advertised on the network or it will be identified as an IP conflict by some network components. To avoid IP address collisions, disable ARP for IP addresses managed by the loopback interface.
Info
Linux is the only OS that supports this configuration. Windows does not. The procedure may vary depending on your Linux distribution.
Info
These steps should be performed on the backend servers being load balanced and not on the HAProxy ALOHA server itself.
-
Manage the VIP through a loopback interface. Specify a
/32or255.255.255.255netmask. For example, below we manage the10.0.0.9VIP through thelo:1loopback interface.nixsudo ifconfig lo:1 10.0.0.9 netmask 255.255.255.255nixsudo ifconfig lo:1 10.0.0.9 netmask 255.255.255.255To check your changes, run
ifconfig:nixifconfig lo:1nixifconfig lo:1outputtextlo:1: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 10.0.0.9 netmask 255.255.255.255loop txqueuelen 1000 (Local Loopback)outputtextlo:1: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 10.0.0.9 netmask 255.255.255.255loop txqueuelen 1000 (Local Loopback) -
Add the following lines to
/etc/sysctls.conf. Then reboot the server.textnet.ipv4.conf.all.arp_ignore=1net.ipv4.conf.all.arp_announce=2textnet.ipv4.conf.all.arp_ignore=1net.ipv4.conf.all.arp_announce=2Info
To test your configuration without rebooting, use the commands below.
nixsudo sysctl -w net.ipv4.conf.all.arp_ignore=1sudo sysctl -w net.ipv4.conf.all.arp_announce=2nixsudo sysctl -w net.ipv4.conf.all.arp_ignore=1sudo sysctl -w net.ipv4.conf.all.arp_announce=2 -
Configure the backend server’s default gateway to be the network’s external gateway.
Do you have any suggestions on how we can improve the content of this page?